What is information security compliance?
Explore the concept of information security compliance and learn why it’s good for business and how to achieve – and maintain it.
Published:
Last updated:

Finding it hard to keep up with this fast-paced industry?
What Is information security compliance?
Information security (InfoSec) compliance is the process of protecting sensitive data from unauthorized access by adhering to industry-specific laws, rules, and standards. In a nutshell, it involves implementing procedures and practices to keep confidential customer information safe.
Understanding information security compliance
At a glance, information security compliance is all about complying with cybersecurity regulations like:
- The CCPA and HIPAA in the U.S.
- The Australian Privacy Act in Australia
- The GDPR in the EU
Standards like these set out guidelines for data security and privacy. They also hold organizations accountable for data breaches by issuing penalties for noncompliance.
That said, cybersecurity compliance is helpful for more than checking a regulatory box. When you get it right, it will protect your data from threats, make your data management more efficient, save time, and make it easier to navigate cross-border selling. It also builds trust with customers, helping you build a strong reputation for security.
Although some may view information security compliance as an unfortunate cost of doing business, it actually can be the key to gaining a strategic advantage. In this practical guide, we’ll go over the key regulations you need to know, explore the benefits, and look at step-by-step tips on how you can put in place a compliance strategy that delivers value to your organization.
The regulatory landscape: U.S. and Australia
We’ll start by taking a look at the most relevant regulations. But first, we need to include a caveat.
While every country has different regulations and frameworks that govern cybersecurity, it’s a good idea to think globally rather than locally when it comes to compliance. Businesses are more interconnected than ever, and data crosses borders in milliseconds. Organizations often fall into the trap of thinking a regulation doesn’t apply to them, and then they discover it does.
As one example, Europe’s GDPR will impact any business that handles the data of EU citizens, even if that business isn’t based in Europe.
To prepare for every eventuality, take a broad view of compliance management rather than focusing on one set of guidelines. International standards like ISO/IEC 27001 can help businesses build a strategy that complies with multiple regulations simultaneously.
Key U.S. regulations and standards
Let’s start with the U.S. data protection regulations and frameworks. Here are the main ones to know:
Key Australian regulations and standards
Next, let’s talk about some of the Australia-specific regulations:
Why compliance is a growth driver
Achieving information security compliance has the potential to drive serious growth for your organization, so it shouldn’t be considered a burden. Here are five benefits to achieving compliance that make it worth the effort:
- Consumer trust: In a recent study, 58% of consumers indicated breaches impacted their trust in a business. On the flipside, showcasing that you’re committed to data security can increase consumer trust in your business, helping you build a strong reputation and stand out from your closest competitors.
- Efficiency: Strong information security compliance will help you build a robust strategy for all aspects of the data lifecycle, from creation to archiving or deletion. This standardized process leads to more productive workflows and streamlined day-to-day efficiency.
- A gateway to global markets: Compliance with global standards like the GDPR or PCI DSS shows that your business is capable of operating on a global scale. If you’re aiming to expand (or want to do so in the future), a bulletproof overarching security strategy will reduce friction as you enter new markets.
- Risk aversion: Cyber attacks are becoming increasingly sophisticated. A strong compliance strategy will protect your data against threats while also equipping you with the tools to avoid disasters in the worst-case scenario. It also protects your sensitive information while helping you manage risk and avoid fines.
- Opportunities: Compliance with relevant regulations is often a prerequisite for business collaboration. From unlocking new investment opportunities to negotiating with vendors, if you can prove you’re compliant, you’ll put yourself in the best possible position to build trustworthy partnerships that accelerate your growth.
Information security compliance isn’t only about bypassing regulatory hurdles – if you can do it right, you’ll also open the door to an array of benefits. Now, let’s dive a little deeper into what ‘doing it right’ actually entails.
What ensures robust information security compliance?
Before we get into the roadmap for achieving compliance, let’s briefly review the key pillars that make for a robust information security strategy:
- Regulatory compliance: At the highest level, businesses need to comply with industry and location-specific laws, such as the CCPA, GDPR, or HIPAA.
- Industry benchmarks: Achieving success often means adhering to industry standards and frameworks like ISO 27001 and the NIST Cybersecurity Framework.
- Technical controls: Security measures are at the heart of compliance. Businesses need to implement firewalls, encryption, and access controls to prevent risk proactively.
- Policies and procedures: Implementing well-documented policies and procedures ensures internal stakeholders are aligned on a clear compliance strategy.
- Staff training: To ensure all staff are prepared to follow policies and uphold data quality, it’s important to educate teams on best practices.
- Incident response planning: If a data breach occurs, a business must know how to respond to it, recover from a disaster, and refine its strategy so it doesn’t happen twice.
- Third-party risk management: Information security goes beyond internal procedures. Companies should also require their partners and vendors to comply with their compliance standards.
- Continuous improvement: Regulatory frameworks need to be flexible. Continuous oversight and regular reporting are necessary for staying agile in the face of new threats.
Now that we’ve looked at the basics, let’s take a look at a five-step roadmap you can use to implement your own information security compliance standard.
A roadmap to achieve and maintain compliance
There are five broad steps we recommend when you’re building a new information security compliance strategy.
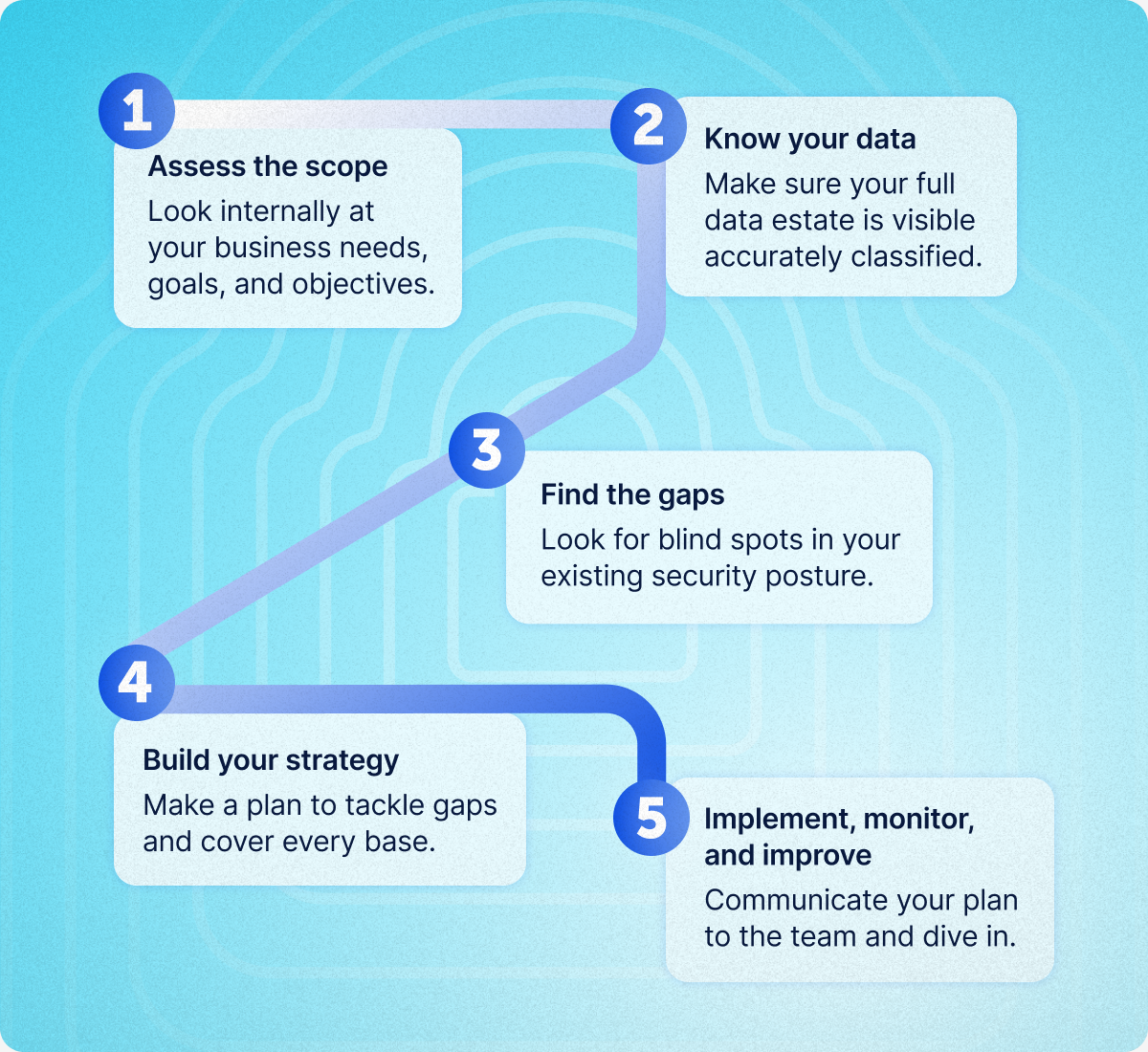
1. Assess the scope
First, you need to look internally at your business needs, goals, and objectives. Here are some questions worth considering:
- Where do you operate? Local legislation dictates the baseline requirements you’ll need to meet. In California, for instance, the CCPA and CCPR will be your bread and butter. But remember that it’s always a good idea to think internationally with your strategy.
- Which kind of data do you handle? You’ll also need to consider the data you’re working with. Cardholder information, for instance, is subject to PSI DSS regulations, whereas health records fall under HIPAA in the U.S.
- What are your scalability goals? Looking to expand into Europe? You’ll need to base your compliance strategy on the GDPR. Want to go public in the next few years? Take stock of the SOX Act. Align your compliance strategy with your long-term objectives.
- What are your goals? Are you looking to reduce cybersecurity risk, expand into global markets, build customer trust, or a combination of these goals? Aside from aligning your team on your strategy’s purpose, a clear goal will also help secure shareholder backing.
You can use your answers here to determine the regulations that are most applicable to your business and to develop a basic roadmap that aligns with your broader business objectives.
2. Know your data
You can’t build a robust data security strategy if you don’t know where all of your sensitive data resides. Focus on building a unified view of all of your siloed information. Then, categorize this data based on its sensitivity to prioritize your information security efforts.
Getting a handle on your information makes it easier to implement secure access controls across your entire data inventory while also reducing friction during access requests. A record management solution can automate compliance by aggregating and classifying your data wherever it lies.
3. Find the gaps
Once you understand your data, you should also evaluate your current security posture. Conduct a risk assessment to identify weak points in your current systems alongside the external and internal threats that are putting your data in danger. Then, categorize these cyber risks based on the likelihood they’ll occur and the potential severity of their impact.
In doing so, you’ll be able to identify which risks pose the biggest threat and optimize your resources accordingly. You should also compare your current security standards with the legal requirements you’re trying to meet to discover gaps you’ll need to prioritize.
4. Build your strategy
Now that you know where your data lies, the compliance risks you face, and the gaps in your current posture, it’s time to build a strategy that covers every base.
Here are some of the key elements you’ll need to consider:
- Involve your stakeholders. People are the biggest weakness when it comes to data security, with human error contributing to 30% of data breaches. Information security is everyone’s responsibility. Be transparent with your stakeholders about the risks you face, the strategy you’re putting in place, and their responsibilities.
- Build your compliance policy. Create a clearly documented policy that outlines the key principles for your compliance strategy. Include information on data handling and management procedures, documentation policies, and any additional employee responsibilities around security and reporting.
- Map out your security controls: What security measures do you need to put in place to protect your sensitive data? Depending on your risk, they may include encryption standards, data backup capabilities, data access controls, multi-factor authentication, and physical security measures like fences, gates, and barriers.
- Develop an incident response plan: You also need to prepare for the worst-case scenario. An incident response plan will make sure you can react quickly if a breach does occur. Clearly identify who is responsible for handling different aspects, outline containment strategies, and determine the notification process for authorities and affected individuals.
Once you have all of the key elements, combine them into a single roadmap and set a timeline to keep your compliance strategy on track. You should also lay out key milestones, assign different internal stakeholders to take ownership at each stage, and inform your third-party associates of the plan.
5. Implement, monitor, and improve
Now you’re ready to implement your strategy. At this point, you should clearly communicate the plan to your team and provide employee training to make sure they understand what their roles are and how to uphold data security best practices.
Remember to establish a routine for monitoring your security posture, risk universe, and compliance efforts. Compliance standards and cyber threats are always evolving, so be ready to reassess your risk and adapt and refine your information security strategy as you gather new information.
Lastly, remember to document the whole process. Many businesses do a great job of implementing security controls, but forget to log the measures they’re taking. Documentation is essential for proving compliance and preparing for audit trails.
Choosing the right tools and partners
Achieving and maintaining compliance isn’t easy when you do it yourself. The best advice we can give is to trust in the right tools and partners to make your journey smoother.
Start with software that automates your recordkeeping and data management processes. RecordPoint can help you identify your sensitive data, classify it based on customizable policies and rules, monitor and alert you to risk in real time, maintain accurate documentation, and more. Learn more about our information security compliance solution.
You may also want to invest in some technical solutions that can help to secure your environment, like:
- Data loss prevention (DLP): Stops sensitive data from leaving your network.
- Encryption tools: Protect data at rest and in transit by encrypting it.
- Identity and access management (IAM): Controls user access.
- Security information and event management (SIEM) systems: Detect threats in real time.
Some businesses may also choose to partner with external specialists like cybersecurity consulting firms and managed security service providers (MSSPs). This can be especially beneficial if you lack the experience or resources to manage compliance in-house.
Common challenges in information security compliance
Let’s wrap things up with some of the key challenges you may need to overcome on your way to developing a robust cybersecurity compliance strategy:
- Resource constraints: Small businesses often lack the time and budget to focus on compliance. Automating key compliance elements can help you do more with less.
- Ad-hoc audits: Maintaining consistency is a serious concern, especially since audits often come up unexpectedly. This is why regular internal checks and audit documentation are crucial.
- Ever-evolving threats: Cyber criminals never stand still. Stay up to date with the newest versions of cybersecurity frameworks like NIST and ISO 27001, which will help you stay one step ahead.
- Security culture: Embedding security into your workplace culture is easier said than done. Lead from the top, invest in training, and develop clear policies and procedures for every member of your team, not just those on the IT team.
- Uniting disparate data: Siloed data scattered across systems, departments, and devices is a source of risk. Tools like RecordPoint unify and classify your records to give you the visibility you need to stay compliant.
Final thoughts
Information security regulatory compliance isn’t just a web of red tape to navigate. It’s an investment that pays dividends toward customer trust and cyber resilience.
By understanding the regulations, assessing your own risk universe, and doing your due diligence to build a strategy that covers every angle, you’ll put yourself in a prime position to reap the full extent of the benefits.
The first step to developing and maintaining a successful compliance program is knowing where your data lies. RecordPoint will automatically collect and classify data from all corners of your digital ecosystem. You can then manage every single data asset in one place. And, with over 900 out-of-the-box connectors, you’ll never need to move a thing from its original location.
Reach out today to book a demo and find out how RecordPoint can help you achieve compliance and maintain it consistently.
FAQs
How often should our organization review its information security compliance posture?
You should do it annually, at a minimum. However, we also suggest conducting reviews following any serious changes. For instance, when you upgrade a system or a regulation receives an update, conduct a review. You should also always review after any cyber incident, big or small.
Is information security compliance primarily a technical or business issue?
It’s both. Compliance is, of course, a technical issue; you can’t achieve watertight security without robust access controls. However, you can’t achieve robust information security compliance without dealing with the human element. Compliance frameworks need to come from the top down. Business policies, procedures, and effective leadership are key to success.
Can a small business effectively achieve information security compliance without a large dedicated team?
Doing it yourself is a challenge. However, by using the right tools and partnering with the right managed services, small businesses can go a long way toward compliance without needing a large internal security team.
What’s the first step if our organization is currently non-compliant?
Conduct risk assessments to find the gaps where your current information security and compliance efforts are falling short, then prioritize these gaps based on their sensitivity and criticality.
How can we ensure employee buy-in for compliance initiatives?
It’s important to relay the ‘why’ behind compliance rather than just the ‘what’. It isn’t just about meeting a regulation. It’s about building trust with customers and protecting the business from threats. You should also make training role-specific and ensure everyone knows their responsibilities.
Discover Connectors
View our expanded range of available Connectors, including popular SaaS platforms, such as Salesforce, Workday, Zendesk, SAP, and many more.



